Zero-Knowledge Encryption
Sovereignty of your thoughts and feelings
Background
At Neelix.IO we believe in full sovereignty of your thoughts and feelings. Same should be the case with digital collaboration mediums, this is why we developed an option to enable zero-knowledge encryption for your reflections in Neelix. This means no one would be able to read your data even if we were required to share raw data from the servers. Provided you choose a good and secure passphrase, it is prohibitive to attempt hacking your data.
Overview
What happens when end-to-end encryption option is enabled:
- Data is encrypted with your passphrase BEFORE it is sent to Neelix;
- Your master passphrase is never communicated , e.g. never leaves your devices;
- No one can read you data; Only you can read it on your device with your passphrase.
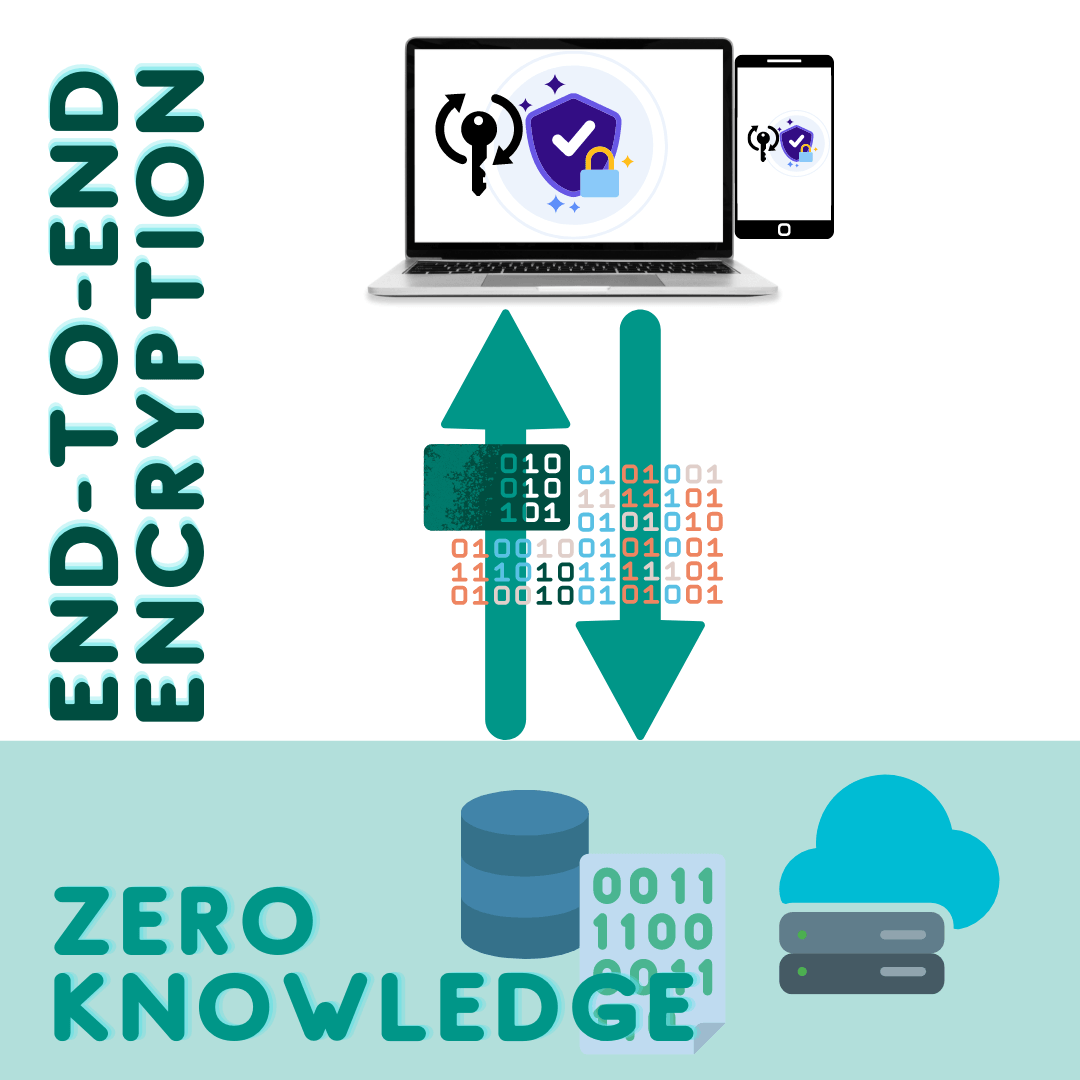
Technical Implementation
All data in Neelix is encrypted when stored in our backend service. Encryption “at rest” secures the actual data within the database and protects backups. Even if an attacker obtains the storage devices containing your data, they won't be able to understand or decrypt it. Find out more here.
Zero-knowledge encryption of specific Neelix data is a different and an additional (optional) feature we developed for securing your data. The process works as follows:
- All protected data are encrypted client-side before being sent to the server for create/update operations using a key shared by all members of your private space
- All protected data are returned encrypted from the server for read options and decrypted client-side using the shared key
- The server never has access to the plain text of protected data
- Shared keys encrypted client-side by each consortium member using their own passphrase
- New users obtain the shared key using client-side public key encryption
- The server never has access to the plain text of the shared key
- Your passphrase is never communicated to Neelix or over internet at all
FAQ
What is the significance of encryption passphrase?
The passphrase is used to encrypt the key needed to encrypt and decrypt protected data. It allows users to maintain absolute confidentiality of their data. No one but consortium members - not even Neelix - will be able to read your protected data.
How secure is the encryption passphrase?
The first principle is that your passphrase is never communicated. What you type is only local to your session. No one can decrypt your data provided your local environment is not compromised and you choose strong enough passphrase. Please ensure not to use rogue add-ons in your web browser. You can use security.org to check the strength of your key.
What if I forget the master passphrase?
NB: This procedure works only if you previously invited someone else to join your private consortium
- Ask to be removed, if there is another user in your private consortium
- Initiate a new access request
- Provide a new passphrase when prompted
Do other users in my Consortium have their own passphrase?
Yes. Each user’s passphrase can and should be different.
What sort of encryption is used by Neelix?
Protected user-generated data and shared keys are encrypted using AES 256. For key exchange between private consortium participants, shared keys are encrypted with RSA 4096.
What data elements are protected by zero-knowledge encryption
The intent is to encrypt data attributes that may contain sensitive feedback or commentary. Neelix zero-knowledge encryption is applicable to following data elements only:
| Record | Attribute |
|---|---|
| Experience post | commentary |
| Comment on experience post | commentary |
| Goals | Name |
| Goals | Description |
| Goals Target | Name |
| Goals Target | Description |
| Linked action | name |
| Time capsule message | commentary and future commentary |
| Retro feedback | commentary |
| Retro feedback comment | commentary |
| Culture profile option | reflection question |
| Culture user feedback | commentary |
What data elements excluded from zero-knowledge encryption
Data elements considered as metadata are not covered by zero-knowledge encryption:
- Space name
- Experience category names
- Activity names
- User profile name
- Quiz configuration data (question names, etc.)
How to Enable Extra Encryption
- Additional encryption can only be enabled at the consortium creation stage
Important
- Consortium with extra encryption enabled will not work with Slack or MS Teams integrations
- The security of the master passphrase and security of your local environment may be your responsibility
Self-reflection
85% of us are either lying to ourselves, in denial or just not seeing ourselves clearly
Happiness
60% of younger people believe I'd be a happier person and physically healthier if I reduced the time I spend on social media
Goals & Resolutions
95% of people confess to at least occasional procrastination
Positive Thinking
average person has about 12,000 to 60,000 thoughts per day.
85% of what we worry about never happens
"One No, can be worth a thousand of Yes's"
Somebody
“When something goes wrong with a computer, you get an error message. When something goes wrong with a human, you get feelings”
Andrew Tarvin (“The Skill of Humor”)
"I didn’t say I liked it. I said it fascinated me. There is a great difference."
Oscar Wilde
"You must always live in love with something unreachable... a person becomes taller because he reaches up"
Maxim Gorky
“The single biggest problem in communication is the illusion that it has taken place.”
George Bernard Shaw
"The value of an idea has nothing whatsoever to do with the sincerity of the man expressing it"
Oscar Wilde


